13+ diffie hellman calculator
One of you is Alice a and one is Bob b. Working with Parameters and Generating.

Pdf Enhanced Diffie Hellman Algorithm For Reliable Key Exchange
Bob chooses a Private Value.

. This group may be Z p or may be the points on. N g Both Alice and Bob each pick a private x and compute a public X g x mod n. Alice computes Public Value.
Public_A 1 mod Bob computes Public Value. If p is a full size real security parameter then dont waste your time on solving discrete logs. It is described in RFC 2631 and Public Key Cryptography Standard PKCS 3.
N g Both Alice and Bob each pick a private x and compute a public X g x mod n. Up to 24 cash back Posted by 2 years ago. Diffie-Hellman operates in a group.
Public_B 1 mod Alice and Bob. This video goes over a simple way of doing Diffie-Hellman with a calculator. If genders dont match thats ok one of you can be Alan and the other.
Lets look at two. Up to 24 cash back DIFFIE HELLMAN CALCULATOR SOFTWARE This is free and unencumbered software released into the public domain for educational purposes. To share a secret key.
With Diffie-Hellman in its most general description there are three different types of objects involved. I want to solve this Diffie Hellman problem. How do you decrypt Diffie Hellman.
17 In the general case for proper security with Diffie-Hellman we need a value g such that the order of g the smallest integer n 1 such that g n 1 mod p is a multiple of a large enough. Its free to sign up and bid on jobs. Encrypt and decrypt a number Select the shared numbers.
Time Complexity Exploration Eulers totient. Diffie - Hellman. Select a large prime number P.
The discrete logarithm problem. Diffie-Hellman D-H is a public key algorithm used for producing a shared secret key. Search for jobs related to Diffie hellman calculator or hire on the worlds largest freelancing marketplace with 20m jobs.
You probably wont be able to recover x. In this version of the discrete logarithm calculator only the Pohlig-Hellman algorithm is implemented so the execution time is proportional to the square root of the. Secret number a p m g.
Alice chooses a Private Value a. For those unfamiliar with Diffie-Hellman or dc or Perl. Select the private key and share the public key.
Oct 30 2017 at 1344. All the program does if you run it as program g x m is output g x mod m where g x and m are given in hexadecimal. Modified 7 years 4 months ago.
Find someone you do not know and introduce yourself. Up to 24 cash back The first step with the Diffie-Hellman algorithm is to ensure that both parties are using the same set of parameters ie.
What Is The Diffie Hellman Key Exchange And How Does It Work Securecoding

Learn Dh In Cryptography Diffie Hellman Key Exchange

Understand Diffie Hellman Key Exchange Infoworld
Guide To The Diffie Hellman Key Exchange Algorithm Its Working Simplilearn

Upgraded Diffie Hellman Key Exchange For Reliable Key Exchange Download Scientific Diagram

Diffie Hellman Key Exchange Protocol Using The Pydhe Python Library The Security Buddy
Guide To The Diffie Hellman Key Exchange Algorithm Its Working Simplilearn
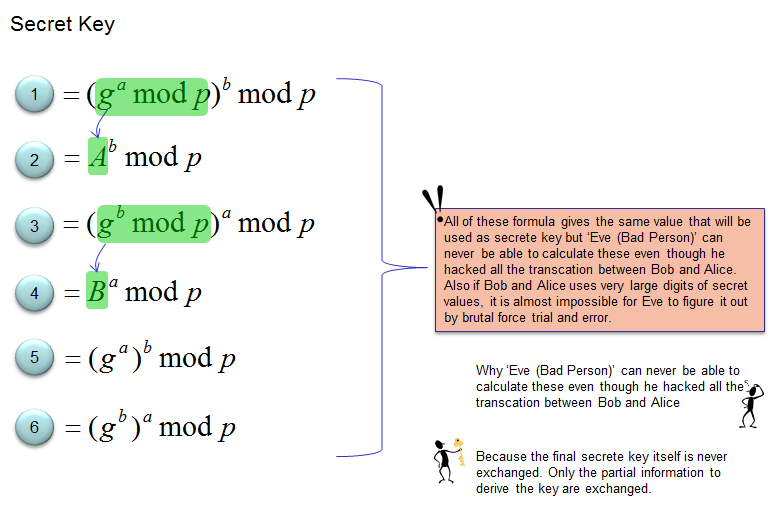
Ip Network Sharetechnote
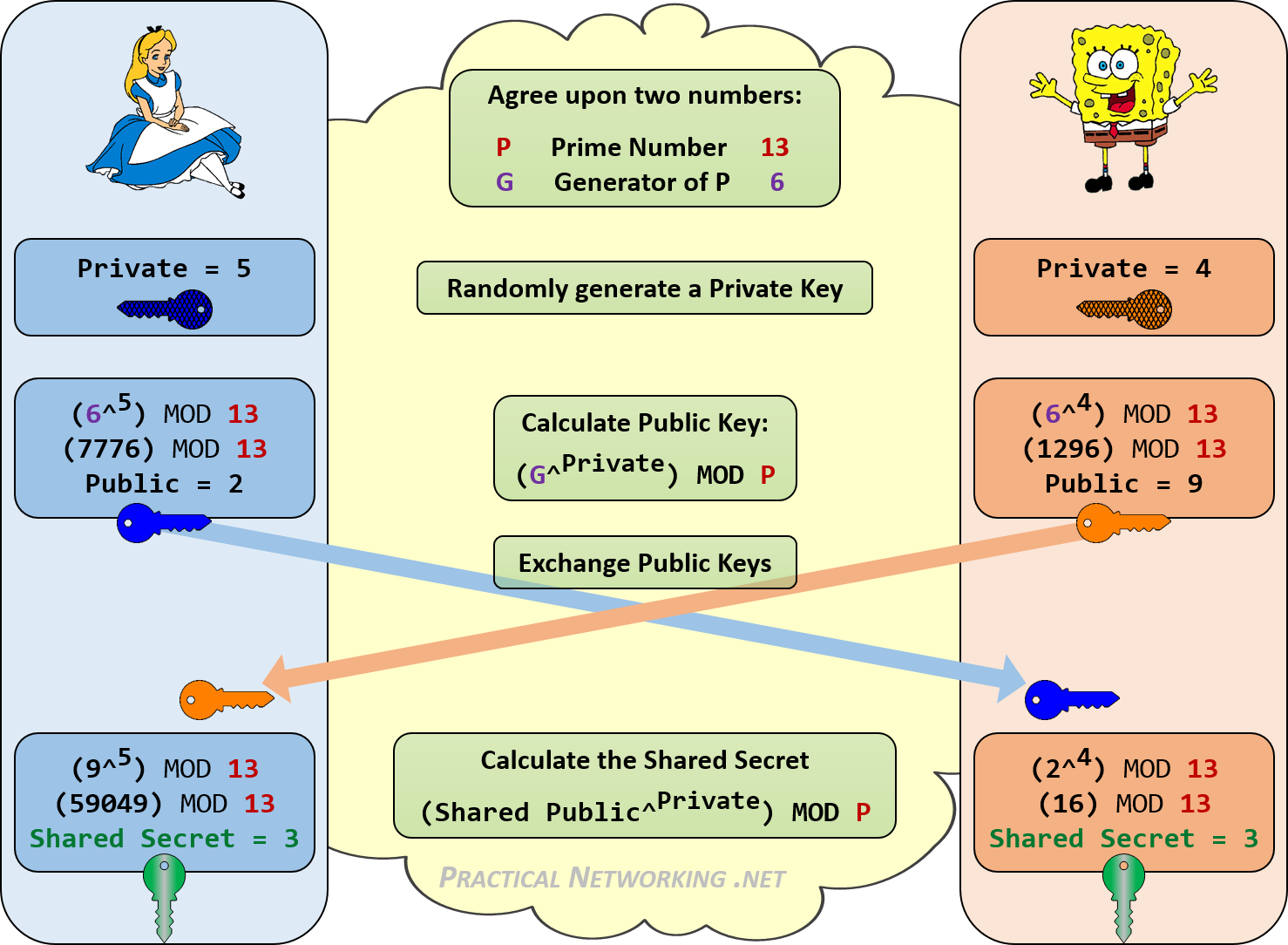
Diffie Hellman Practical Networking Net

Understand Diffie Hellman Key Exchange Infoworld

Diffie Hellman Key Exchange For Authentication Download High Resolution Scientific Diagram
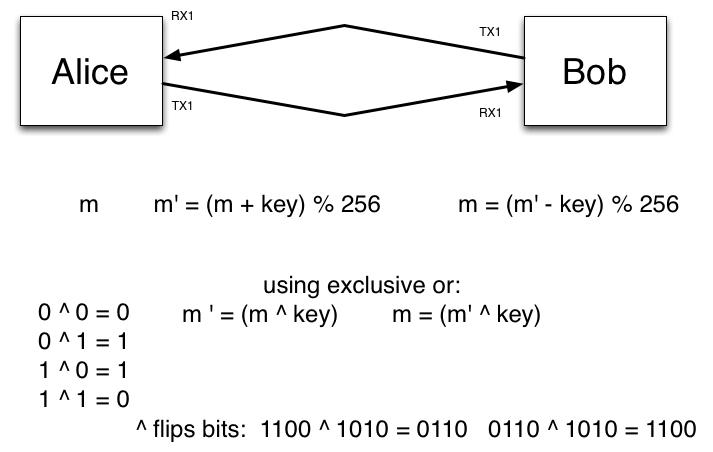
Tangible Computing 7 Diffie Hellman Key Exchange

Diffie Hellman Key Exchange In Short The Diffie Hellman Is A By Cory Maklin Towards Data Science

Diffie Hellman Key Exchange Video Khan Academy
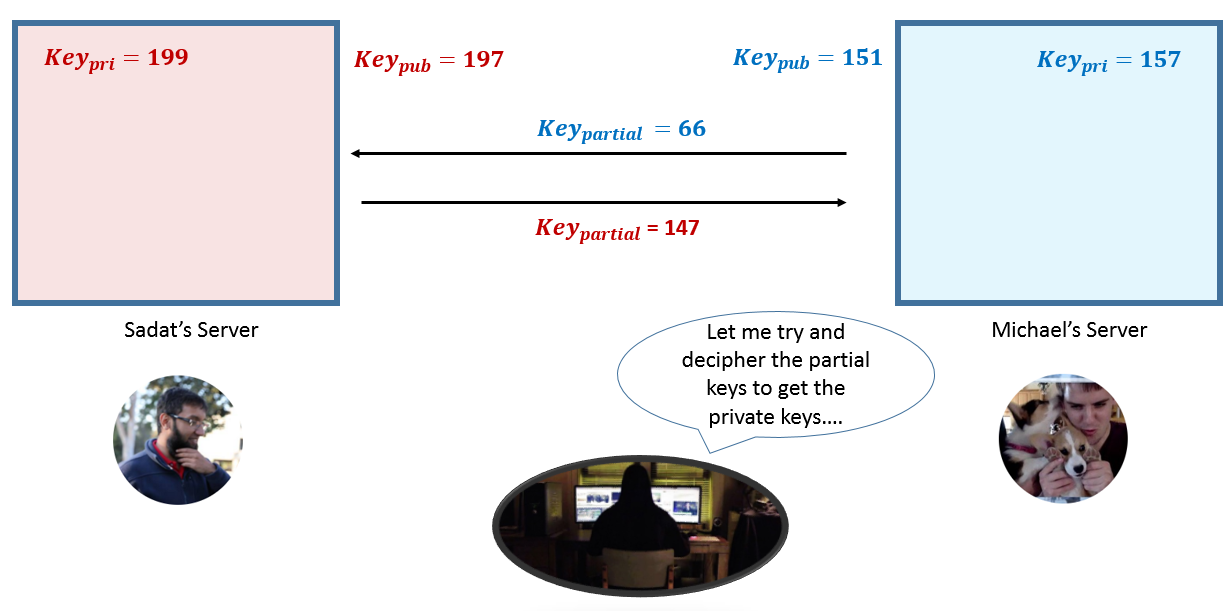
Diffie Hellman Key Exchange Explained Python By Syed Sadat Nazrul Medium

Diffie Hellman Key Exchange Vs Rsa Encryption Consulting

Diffie Hellman Key Exchange Vs Rsa Encryption Venafi